Home / DSRAZOR for Windows
Best Practices for Active Directory and Risk Analysis
Identifying vulnerabilities | Avenues to Compromise
"The easiest and least-detectable way to gain unauthorized access is to leverage someone's (or something's) authorized access."By assessing your Active Directory and Windows File Systems for risks you will be better prepared to document your findings and discover risks to your Active Directory infrastructure.
With DSRAZOR for Windows you will be able to quickly identify and correct the following conditions:
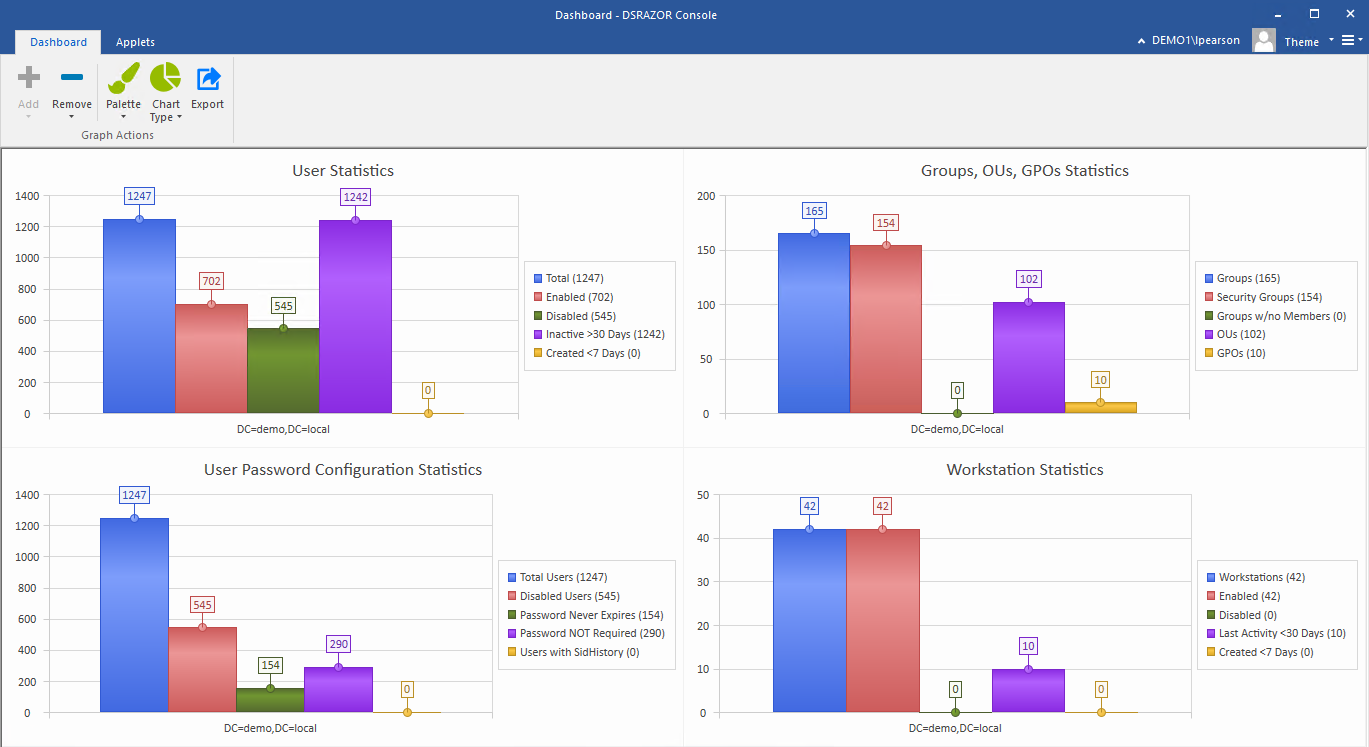
- STALE USER ACCOUNTS [defined as being no logon for a specified number of days] - Are there accounts of past employees that should of been removed or disabled? Do stale accounts still have privileged access to Active Directory and your File Systems? Do user accounts exist with no expiration date?
- NEVER LOGGED ON - Could these accounts be defined with a "default" password? Perhaps no password? Because no one is apparently using these accounts, if compromised, how long until you notice since no one else will notice?
- NON-EXPIRING PASSWORD - Over time passwords may become known due to various reasons, by enforcing passwords expire at a specified interval, your users will be required to use unique new passwords, especially those with elevated privileges by way of direct assignment and/or group memberships.
- USERS WITH NO GROUP MEMBERSHIP - What is the purpose of these accounts? Perhaps they are service accounts? If not, how are each being used and do each exist for a legitimate use?
- EMPTY GROUPS - What is the purpose? Remove unneeded/unnecessary groups that could be comprised for other purposes.
- INCOMPLETE USER DEFINITIONS - Considering other potential issues are users with no description, no title, no department, no manager, and no group membership. Each can be quickly located, reported and modified with DSRAZOR for Windows.
Reducing the Active Directory Attack Surface
"Regular" users who have Active Directory accounts in a domain are, by default, able to read much of what is stored in the directory, but are able to change only a very limited set of data in the directory.Users who require additional privilege can be granted membership in various "privileged" groups that are built into the directory so that they may perform specific tasks related to their roles, but cannot perform tasks that are not relevant to their duties. Organizations can also create groups that are tailored to specific job responsibilities and are granted granular rights and permissions that allow IT staff to perform day-to-day administrative functions without granting rights and permissions that exceed what is required for those functions.
Within Active Directory, four built-in groups are the highest privilege groups in the directory (Enterprise Admins, Domain Admins, Administrators, and Schema Admins), although a number of additional groups and accounts are likely to be also protected and membership regularly reviewed for proper inclusion.
If a malicious user obtains privileged access to an Active Directory (hosted by one or more domain controllers), that user can modify, corrupt, and destroy the Active Directory database, and by extension, all of the systems and accounts that are managed by Active Directory.
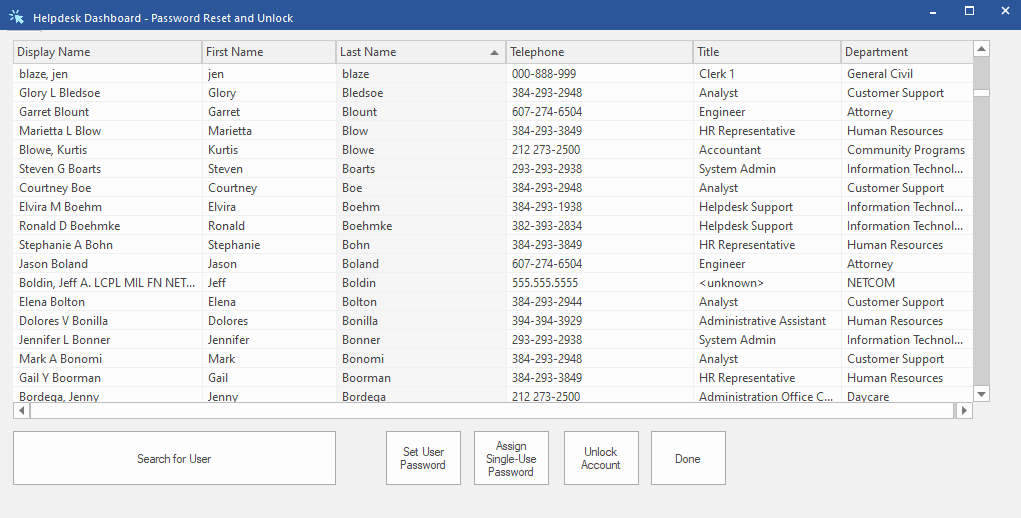
DSRAZOR for Windows Zero-Privilege Helpdesk provides you with a superior method of implementing Least-Privilege Roles-Based Administration to reduce the risks associated with use of highly privileged accounts for day-to-day administration.
Monitoring Active Directory for Signs of Compromise
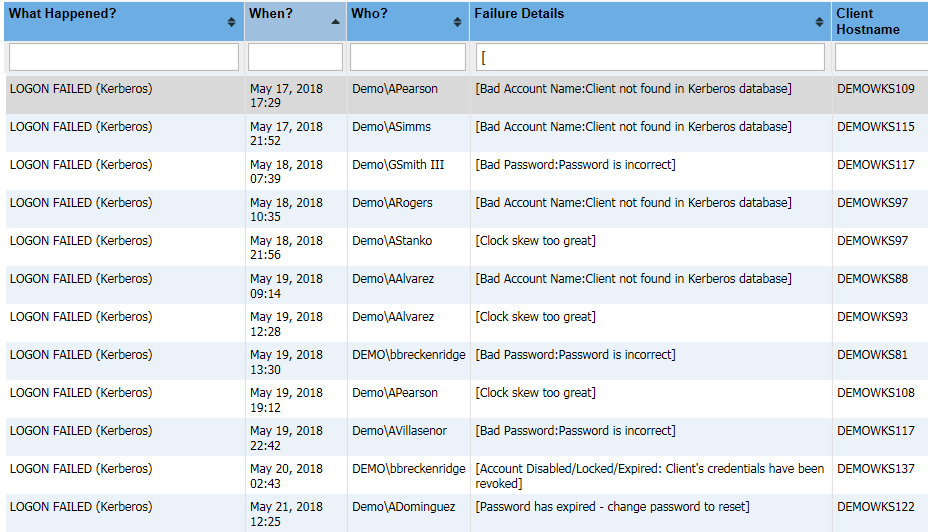
Questions about auditing often arise only after a significant incident occurs. For example, basic auditing may be enabled but if the system is not configured to audit for a particular change, due to a lack of planning, that information will not be collected.In the past, auditing of access to information could be summarized as a desire to know and an attempt to be secure. Now, as organizations-and the senior management responsible for them-are being held legally accountable for loss of information or lack of proper safeguards, it is critical for IT administrators to familiarize themselves with the regulations that may be applicable to their environments.
CPTRAX for Windows provides an easy-to-use method to ensure security access auditing is implemented and ready to provide necessary documentation including real-time alerts of significant security events. For instance, CPTRAX has been used to watch for ransom-ware infiltrations as it crawls through protected file systems enabling administrators, via real-time email alerts, to immediately act. CPTRAX can be configured to watch for account lockouts, patterns of failed password activity and even changes to your sensitive groups for membership changes and permissions elevations. Please click here for further details (https://www.visualclick.com/content/cptrax-for-windows-active-directory.htm).
Developing a long-term security plan
Ensuring compliance with your organization's Active Directory implementation of best practices is simplified with DSRAZOR for Windows. Consistent user account creation including mandatory initial random complex password assignment, proper assignments of required group membership, correct specification of department, manager and more put you in charge of your Active Directory access control.DSRAZOR for Windows including the Zero Privilege module provides auditing of all completed actions so you know who performed each action with full details.
DSRAZOR helps you forge closer relationships between your IT team and other departments. If your IT team retains tight controls such as implementation of various workflow processes that rely on IT team members to be performed, DSRAZOR for Windows Zero Privilege functionality can relieve that burden by allowing the IT team to safely and securely delegate elevated permissions within Active Directory and Windows File Systems without granting native permissions.
For instance, utilizing DSRAZOR's Zero Privilege, the HR team (https://www.visualclick.com/content/dsrazor-hr-enabling-user-account-management.htm) and/or unit managers can have timely and consistent control of user account creation for their respective teams.
DSRAZOR gives you the power to reduce IT staff workloads, potentially savings can result by reducing or better utilization of full time employees (FTE) while improving IT governance by automatically documenting changes to your Active Directory and File Systems. Additionally, when IT staff turnover occurs, your implementation of DSRAZOR remains the bedrock of consistency.
Additionally, with DSRAZOR for Windows you will receive the following reports:
- Privileged Identity Discovery Reports including all objects with create, delete, write, or any other Active Directory change permissions and objects they control + Ability to remove those permissions
- Privileged Identity Discovery Reports including all objects with create, delete, write, or any other change permissions and File System objects they exert that control over + must include local workstation file systems too and shares
- Local Group accounts members report
- AD accounts last logon report
- Local User accounts last logon report
- AD Password Strength report (i.e. password never expires, when password expires, etc.)
- AD Group Membership Report
- Accounts that are locked, disabled, expired, have never logged in, that never expire
- Accounts unused for X days
- Accounts where last logon failed
- Accounts with Dialin permission
- Active Directory Last Logon Report by DC
- Active Directory Objects with a NULL ACL (no access restrictions)
- Active Directory Objects with GPO(s) defined
- Active Directory objects with the "Send As" privilege
- Active Directory Trustees (users and groups)
- Active Directory Trustees with Admin privileges
- Active Directory Account Security Details Report
- Duplicate Active Directory Object names
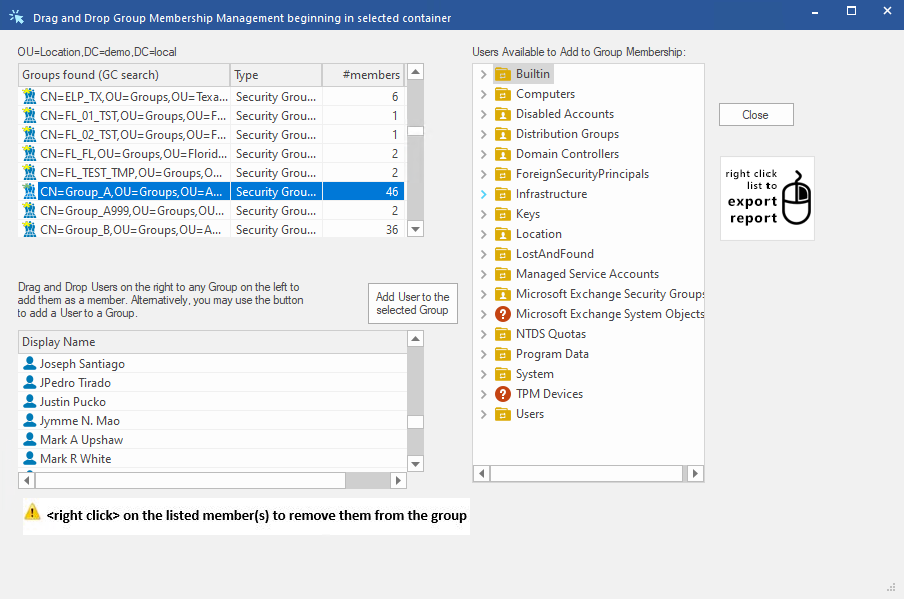
- Group Membership
- Groups that are members of Groups
- Objects with Group Policy Objects defined and list any account policies
- Users created in the last 'n' number of days
- Users that are disabled
- Users that never expire
- Users whose last logon failed
- Users who have never logged in
- User accounts that are locked
- User accounts that are expired
- User accounts with password problems where you can define which password problems to report on
- ACL Documentation per File System Object or Share
- Directories/Files with no owner (orphaned SID)
- Directory/File System Objects with a NULL ACL (no access restrictions)
- Directory/File Ownership
- Document Share Permissions
- File System Objects where Permission Inheritance is Blocked
- Find Duplicate File System Object Names
- Find Files unused for past 365 days
- and much more.
When you utilize our Create My Solution service you will receive further reports to your specifications that will increase your ability to customize and augment your Active Directory and File System best practices. Customization without custom code.
Once reporting is complete, DSRAZOR for Windows will remain an effective tool to further your efforts to maintain a secure Active Directory environment.
Details of additional DSRAZOR functionality:
Get a free trial of our tools today!
Our products include 1 YEAR of our world class support!
Unlimited Training
We'll make sure you can take advantage of everything our products have to offer.
Unlimited Support
Our rapid-response support team can assist with any questions you may have.
Custom Applet Design
Need more? Just ask! We'll create a custom solution that fits your needs.